Firmware Vulnerabilities Report
The Firmware Vulnerabilities Report in Site24x7's Network Configuration Manager (NCM) gives administrators complete visibility into security weaknesses affecting network devices. It consolidates insights from multiple perspectives—by vulnerabilities, devices, and firmware versions—so administrators can quickly assess their exposure, prioritize remediation, and maintain compliance.
The report includes three views:
- Vulnerabilities (CVE) Report
- Exposed Devices Report
- Affected Firmware Versions Report
Use cases
- Identify and track vulnerabilities across all monitored NCM devices.
- Prioritize remediation by focusing on critical vulnerabilities that impact production.
- Assess your exposure by identifying which devices and firmware versions are vulnerable.
- Ensure compliance with internal and external security requirements.
- Monitor your remediation progress with patch status and device state updates.
Generating the report
- Log in to your Site24x7 account.
- Navigate to Reports > NCM Device > Firmware Vulnerabilities Report.
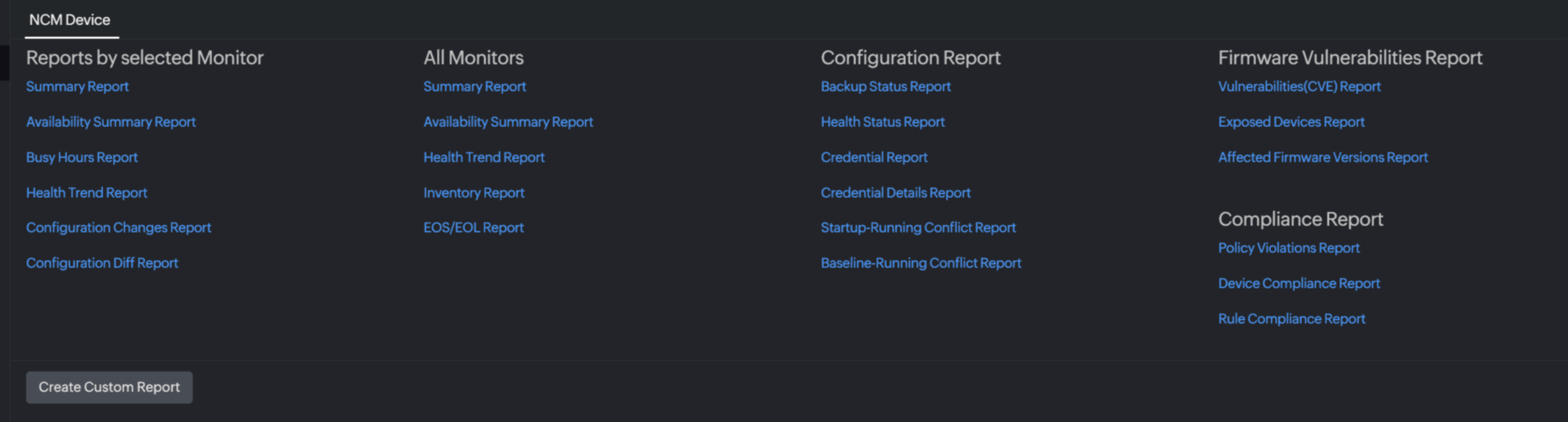
- Select the desired report: Vulnerabilities (CVE) Report, Exposed Devices Report, or Affected Firmware Versions Report. You can also toggle between these options from within any report view.
- Expand records for detailed information or click Expand View to view all records at once.
- Vulnerabilities are categorized as Critical, Important, Moderate, or Low. Click a category name to view only the vulnerabilities in that category.
- Use column headers to sort data in ascending or descending order.
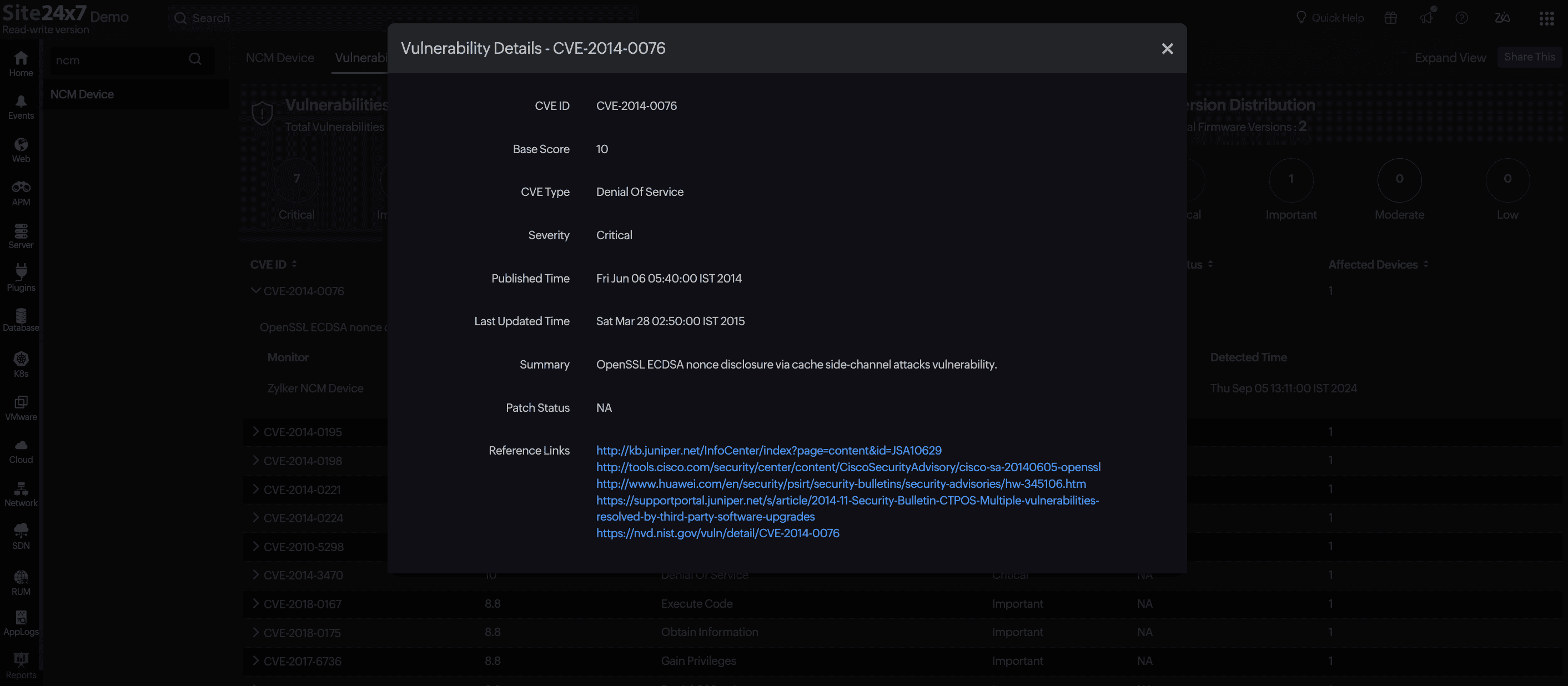
- Click View Details or any specific CVE ID to view the Vulnerability Details.
- Click the Share This button to export the report as a CSV or PDF file, email it, or schedule it to be generated at regular intervals.
Report types
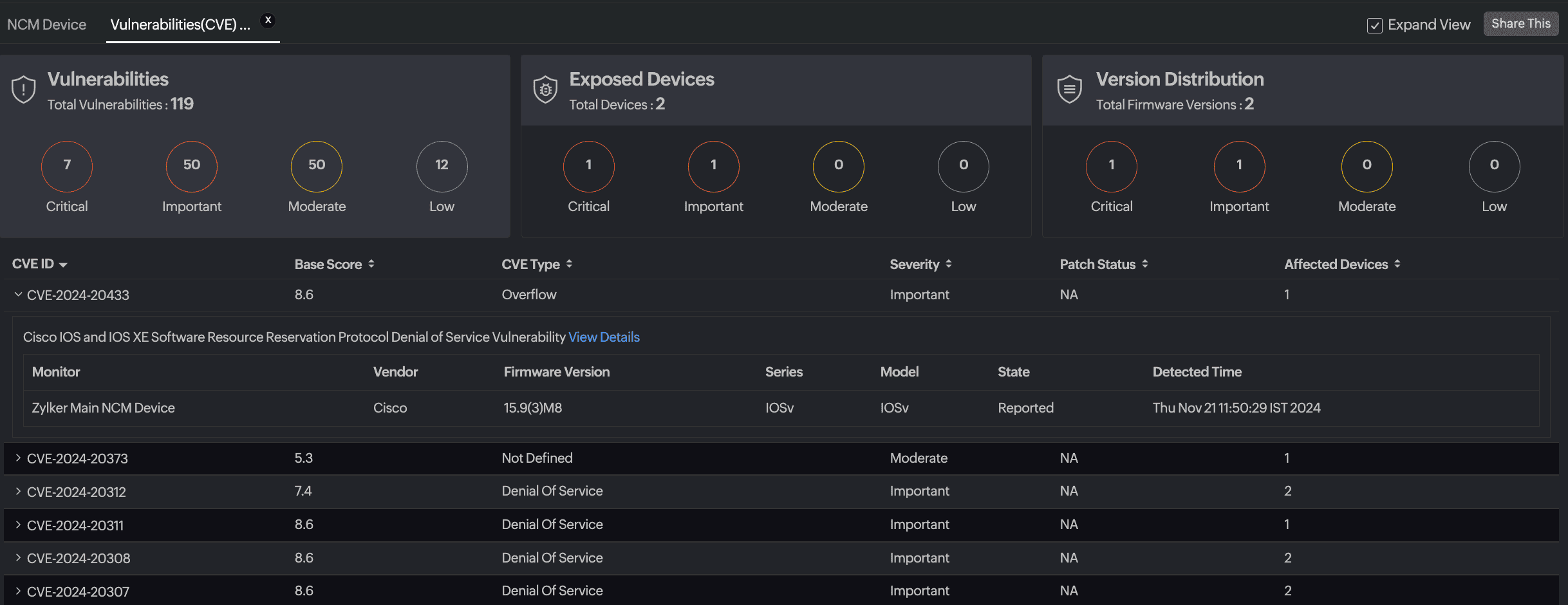
The Firmware Vulnerabilities Report is divided into three sections: Vulnerabilities, Exposed Devices, and Version Distribution. Each offers a different perspective on detected vulnerabilities and their impact.
- Vulnerabilities (CVE) Report
This report provides a list of all vulnerabilities detected across monitored devices.- Vulnerabilities: Click a Severity value (e.g., Critical or Important) to filter vulnerabilities by the category.
- Sortable columns
- CVE ID
- Base Score (CVSS)
- CVE Type
- Severity
- Patch Status
- Affected Devices
- Vulnerability Details (CVE-level insights)
- CVE ID: The unique identifier (e.g., CVE-2014-0076)
- Base Score: The CVSS score (0–10)
- CVE Type: The type of vulnerability (e.g., Denial Of Service or Information Disclosure)
- Severity: The vulnerability category (Critical, Important, Moderate, or Low)
- Published Time: The date of the initial publication
- Last Updated Time: The most recent CVE update
- Summary: The description of the vulnerability and its impact
- Patch Status: The availability or application of a fix
- Reference Links: The vendor advisories and security databases
- Exposed Devices Report
This report shows which devices are impacted by vulnerabilities, grouped by the severity.
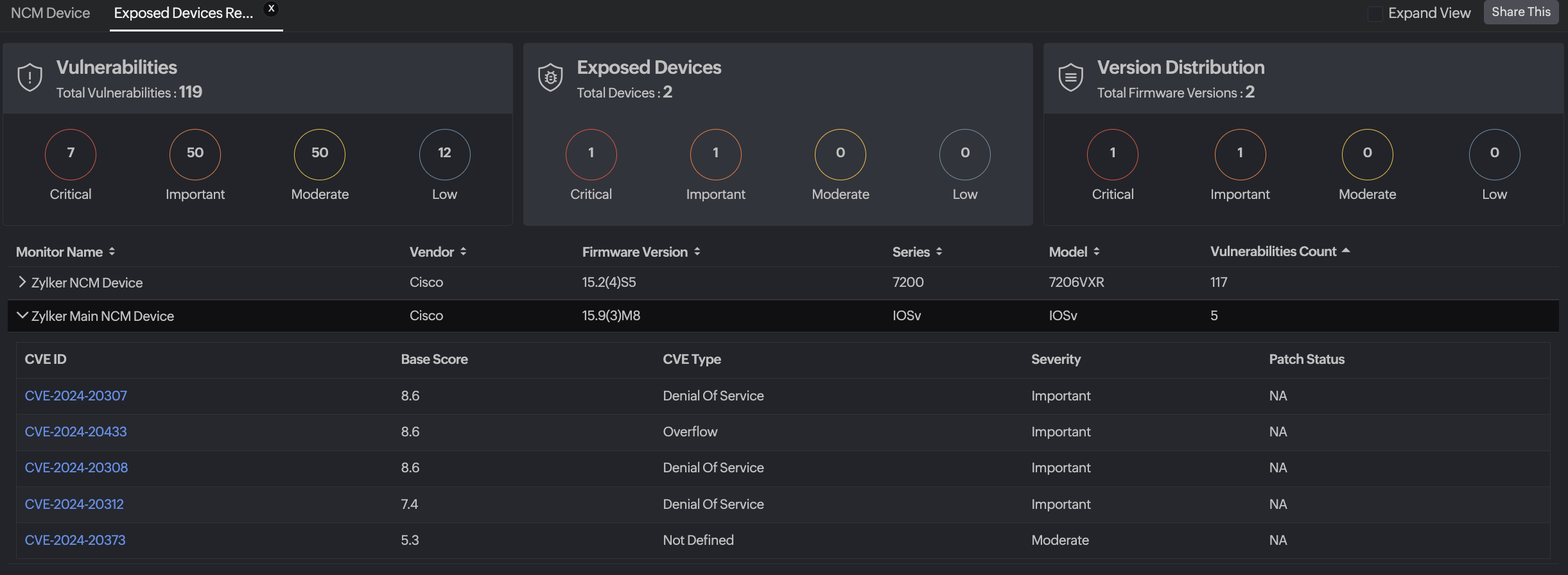
- Sortable columns
- Monitor Name
- Vendor
- Firmware Version
- Series
- Model
- Vulnerabilities Count
This view helps you quickly identify devices that need immediate patching.
- Sortable columns
- Affected Firmware Versions Report
This report displays vulnerabilities grouped by the firmware version to help you assess the scale of the exposure.
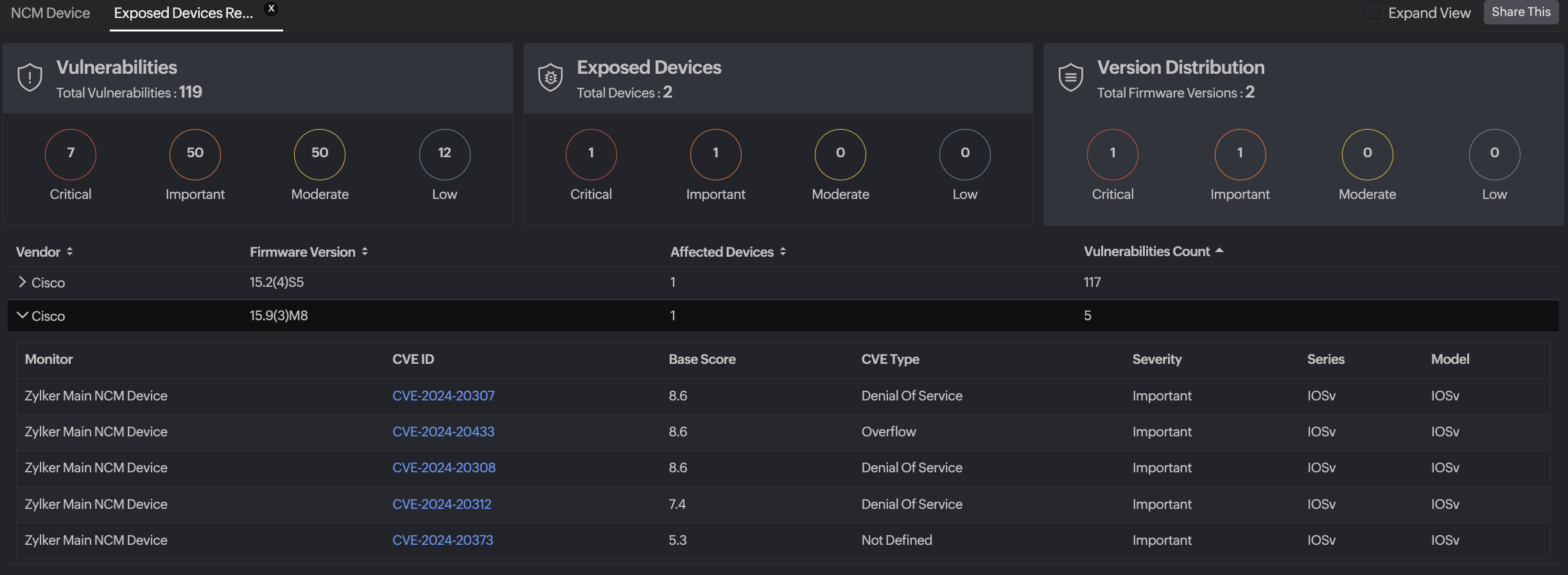
- Sortable columns
- Vendor
- Firmware Version
- Affected Devices
- Vulnerabilities Count
This view is especially useful for planning bulk firmware upgrades when multiple devices run the same vulnerable version.
- Sortable columns
A comparison of the report types
| Report type | Focus area | Use case |
|---|---|---|
| Vulnerabilities (CVE) Report | A CVE-centric view of vulnerabilities | Understanding the scope, severity, and details of individual vulnerabilities. |
| Exposed Devices Report | A device-centric view | Identifying which specific devices are at risk and need patching. |
| Affected Firmware Versions Report | A firmware-centric view | Planning bulk upgrades when multiple devices share a vulnerable firmware version. |
Best practices
- Address critical vulnerabilities first.
- Focus on CVEs that are marked Critical and are affecting production devices.
- Check the firmware version distribution.
- If multiple devices share the same vulnerable version, plan bulk upgrades.
- Review patch statuses regularly.
- Apply available patches promptly to reduce exposure.
- Audit and document remediation.
- Export reports for compliance and track resolved versus pending issues.
- Enable automated alerts.
- Configure notifications to receive updates whenever new vulnerabilities are detected.