Baseline-Running Conflict Report
The Baseline-Running Conflict Report compares a device’s running configuration with a predefined baseline configuration. This ensures that the device stays aligned with your approved network standards and security policies.
Use cases
-
Detect unauthorized configuration changes: The report highlights any deviation from a predefined, approved baseline. This is critical for spotting modifications made outside of change windows or without proper approvals.
-
Enforce configuration standards: By comparing to a clean, approved baseline, ensure all devices maintain organization-wide configuration standards, such as specific SNMP settings, access control lists (ACLs), or routing policies.
-
Pass internal or external audits: Proof of configuration consistency and policy enforcement during audits by IT, security, or regulatory bodies.
Generating the Baseline-Running Conflict Report
-
Log in to your Site24x7 account.
-
Navigate to Reports > NCM Device > Baseline-Running Conflict Report in the All Monitors section.
-
The report displays a list of NCM monitors with details such as Display Name, IP Address, Deleted lines, Modified lines, Added lines, Backup Status, and more.
-
Use the Group by drop-down to organize devices based on parameters like Vendor, On-Premise Poller, Device Template, and more.
-
Use the Filters option to narrow down the report by backup status, time range, or specific devices.
-
Click the Share This button in the top-right corner to export the report as a CSV or PDF, email the report, or schedule it at regular intervals.
-
Hover over a device name and click the open in a new tab
 icon to view the monitor summary page for that device.
icon to view the monitor summary page for that device. -
Click the column
 icon to customize additional columns in the Baseline-Running Conflict Report.
icon to customize additional columns in the Baseline-Running Conflict Report.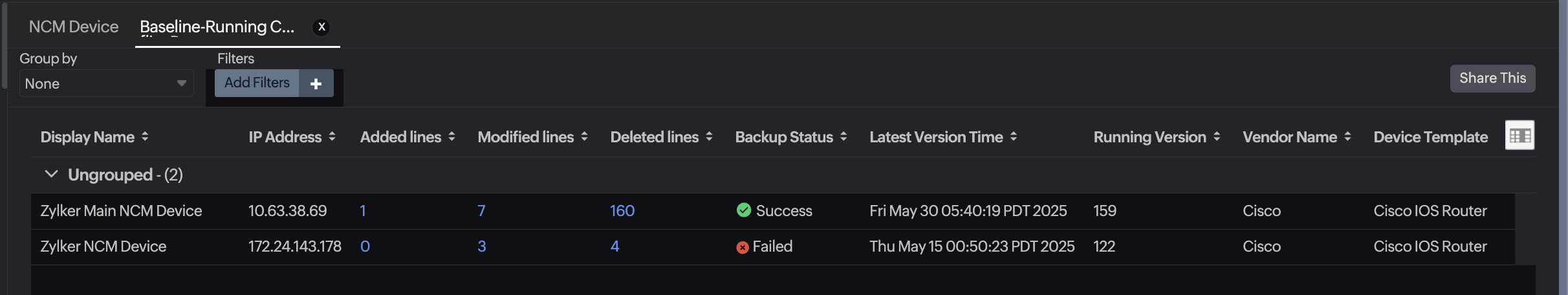
Report columns
| Column | Description |
|---|---|
| Display Name | User-defined name for the device in NCM |
| IP Address | The IP address of the NCM device |
| Deleted Lines | The total count of deleted lines in the baseline running configuration compared with the current running version |
| Modified Lines | The total count of modified lines in the baseline running configuration compared with the current running version |
| Added Lines | The total count of added lines in the baseline running configuration compared with the current running version |
| Backup Status | Indicates whether the latest backup succeeded or failed |
| Latest Version Time | Timestamp of the most recent version change |
| Running Version | The version number of the current running configuration |
| Vendor Name | Manufacturer of the device (e.g., Cisco) |
| Device Template | Template used to classify the device (e.g., Cisco IOS Router) |
| On-Premise Poller | The On-Premise Poller that performed the backup operation |
| Series Number | Series information of the device model |
| Model Number | Device model identifier |
| Protocol Name | The communication protocol used for configuration backup or monitoring (for example, SSH, SSH-TFTP, etc,.) |
| Credential Name | The credentials used for the device |
| OS Version | Operating system version running on the device |
| System Description | General device description |
| OS Type | The type of operating system installed on the device (for example, iOS, NX-OS) |
| Startup Version | The version number of the current startup configuration |
Best practices
-
Define baselines for all critical devices.
-
Review and update baselines after authorized changes.
-
Use this report as part of the regular configuration audit routines.