Critical services need constant attention to prevent threat actors from exploiting vulnerabilities. For example, imagine a power plant with a firmware vulnerability in its control systems, and the vulnerability has been ignored because it seems harmless. What would happen if this vulnerability was exploited?
Along with the immediate health and safety concerns, the economic impact could be substantial, with a potential loss of millions of dollars in lost productivity and recovery efforts. These disruptions present major obstacles for vital services and endanger the public.
For companies responsible for critical infrastructure, firmware vulnerabilities are a persistent threat that often gets overlooked in favor of more obvious software issues. But why do firmware vulnerabilities remain such a blind spot, and how can organizations strategically mitigate these risks?
What are firmware vulnerabilities?
Firmware is the foundational software embedded in hardware devices, from industrial control systems to IoT sensors and network routers. While it plays a crucial role in enabling hardware functionality, its lower-level nature often makes it harder to patch and secure compared to regular software. Firmware vulnerabilities can allow attackers to bypass traditional security measures, gain access, and even render hardware unusable.
As a network administrator, you should check the following regularly:
- How often does your organization audit the firmware of critical devices?
- Do you know if your vendor provides regular firmware updates and security patches?
- Are you tracking firmware versions across your infrastructure?
The high stakes of firmware vulnerability management in critical infrastructure
The impact of firmware vulnerabilities can be catastrophic, especially for sectors like energy, healthcare, transportation, and utilities. Consider these examples:
- Energy sector: A power grid's substations use control systems running on embedded firmware. If exploited, an attacker could cause widespread outages or even physical damage to equipment.
- Healthcare: Medical devices such as infusion pumps and imaging systems rely on firmware. A breach could jeopardize patient safety and compromise sensitive data.
- Transportation: Firmware vulnerabilities in traffic management systems or railroad control mechanisms can lead to safety risks and logistical chaos.
Real-world example: VPNFilter malware attack on network devices
The 2018 VPNFilter malware attack exploited firmware vulnerabilities in over half a million network devices, including routers from major vendors like Linksys, MikroTik, Netgear, and TP-Link. This attack allowed cybercriminals to intercept sensitive data, execute destructive commands, and persist after the device reboots. These incidents underscore the urgency of monitoring and securing firmware to prevent large-scale disruptions.
What are the challenges in managing firmware vulnerabilities?
In an environment where cyberthreats are growing aggressively, managing firmware vulnerabilities is quite challenging. Enterprises face several hurdles:
- Lack of visibility: Many organizations do not have an inventory of the firmware running on their devices, let alone know its version.
- Complex patching processes: Firmware updates often require manual intervention and downtime, which can disrupt critical operations.
- Vendor dependency: Enterprises rely on hardware vendors for patches, and delays can leave vulnerabilities exposed for extended periods.
- Supply chain risks: Firmware vulnerabilities may be introduced during manufacturing, especially with third-party components.
Ask yourself:
- Are you prepared for the operational impact of applying firmware patches?
- Have you assessed the risk of unpatched firmware in your supply chain?
A strategic approach to firmware vulnerability management
To address these challenges, enterprises need a well-rounded strategy that includes:
- Inventory management: Start by monitoring all hardware devices within your infrastructure and maintaining a detailed inventory of their firmware versions.
- Vulnerability assessment: Regularly scan for known vulnerabilities in firmware and prioritize remediation based on risk.
- Patch management: Implement a structured process for testing and applying firmware updates, ensuring minimal disruption.
- Vendor collaboration: Work closely with hardware vendors to stay informed about updates and security advisories.
- Monitoring and alerts: Set up real-time monitoring to detect unauthorized firmware changes or anomalies.
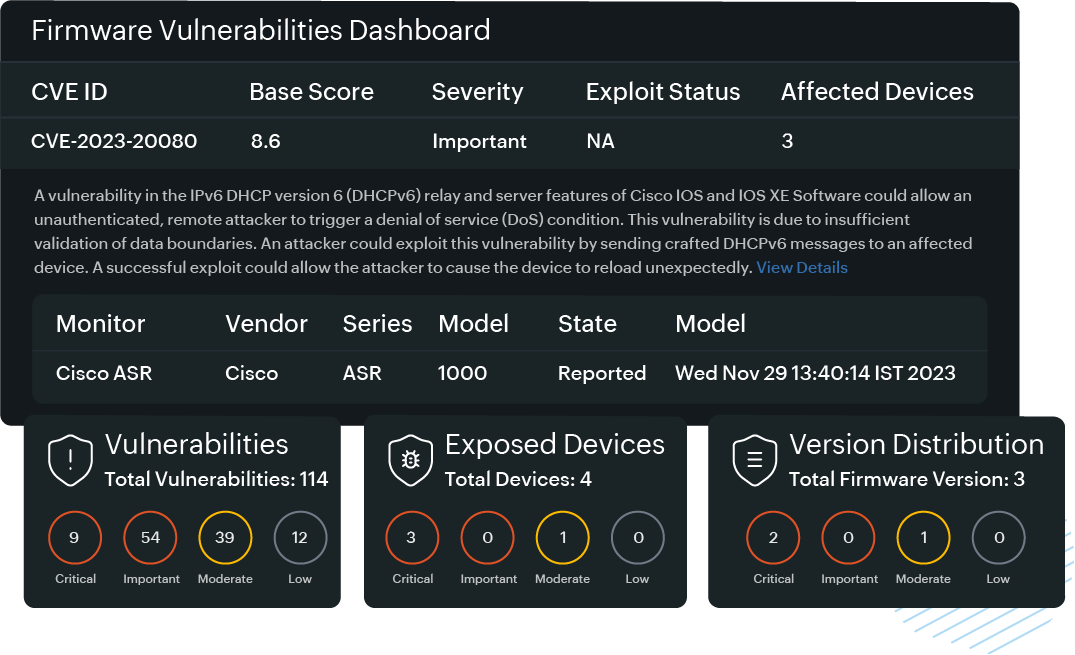
How Site24x7 helps enterprises manage firmware vulnerabilities
Site24x7 provides a unified platform that helps enterprises maintain robust security for their critical infrastructure. Here's how:
- Comprehensive device management: Site24x7's network configuration manager (NCM) detects hardware devices and provides detailed insights into their firmware versions. This visibility is key to identifying outdated or vulnerable firmware.
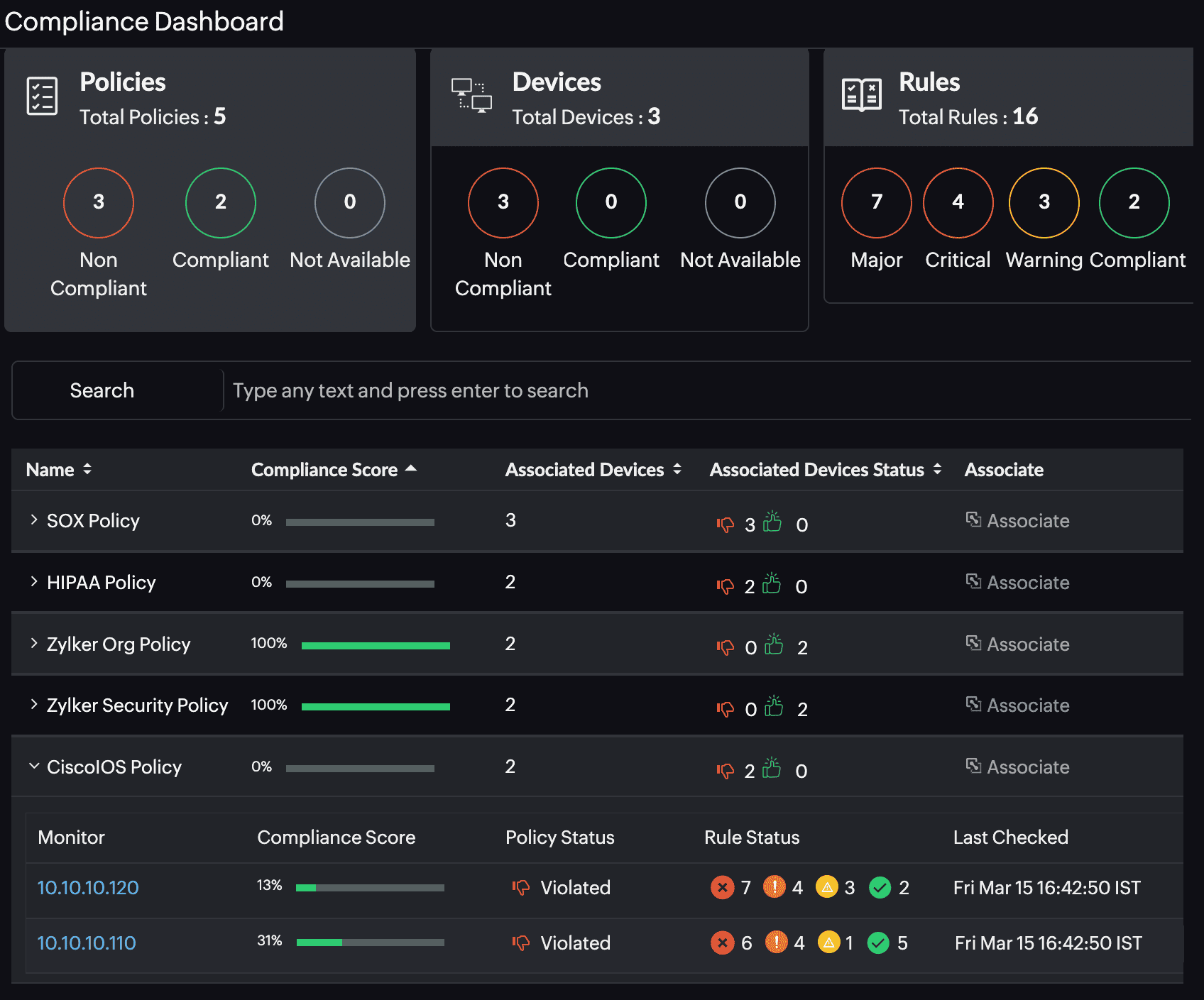
- Compliance made easy: Check for network compliance violations for standards like Cisco iOS, SOX, HIPAA, or even custom organizational policies.
- Vulnerability scanning: By comparing with data from the National Institute of Standards and Technology (NIST), Site24x7 can help you identify known firmware vulnerabilities and prioritize them based on severity and impact.
- Automated alerts: Get real-time notifications for firmware-related issues, such as unauthorized changes or anomalies in device behavior.
- Comprehensive dashboard: Site24x7's intuitive dashboards allow IT teams to track firmware vulnerabilities, patch availability status, and overall vulnerabilities across the network from a single pane of glass.
- Integration with IT workflows: Use Site24x7's integrations with ITSM tools to streamline patch management and coordinate with vendors.
Use case: Enhancing cybersecurity in smart city infrastructure
A city implementing smart infrastructure—including IoT-enabled traffic lights, public Wi-Fi networks, and energy-efficient building systems—can benefit from Site24x7's capabilities. By using Site24x7 to monitor all connected devices, city administrators can:
- Identify firmware versions across thousands of IoT devices.
- Receive alerts when vulnerabilities are detected in critical systems, such as traffic management controllers.
- Coordinate firmware updates with vendors while minimizing service disruptions.
This proactive approach ensures the city's infrastructure remains secure against evolving threats, protecting residents and maintaining operational continuity.
Questions to drive action in your organization
- When was the last time you updated the firmware across your critical devices?
- How would a firmware breach impact your operational continuity?
- Do you have the tools to monitor and manage firmware vulnerabilities effectively?
Safeguarding critical infrastructure from hidden threats
Firmware vulnerabilities may be less visible than software issues, but they pose equally significant risks. Enterprises can protect their critical infrastructure and ensure operational resilience by adopting a strategic approach to firmware vulnerability management and leveraging tools like Site24x7. Don't wait for a breach to take action—the time to prioritize firmware security is now.

